 Researchers from Phylum, a cybersecurity company that monitors the software supply chain to detect and report threats, have discovered more than two dozen Python packages in a PyPI repository that deliver malware that extracts and steals your information. Most of the identified packages contained an obscure code that drops “W4SP” to steal information on infected machines, while others use malware allegedly created for “educational purposes” only. The company identified 29 Python packages containing the W4SP information thief.
Researchers from Phylum, a cybersecurity company that monitors the software supply chain to detect and report threats, have discovered more than two dozen Python packages in a PyPI repository that deliver malware that extracts and steals your information. Most of the identified packages contained an obscure code that drops “W4SP” to steal information on infected machines, while others use malware allegedly created for “educational purposes” only. The company identified 29 Python packages containing the W4SP information thief.
The Asylum researchers report that the affected packages are typos, i.e. actors threatening to publish them on purpose call them similar to legitimate Python libraries, hoping that developers trying to fetch the real library will make a misspelling and inadvertently fetch one. malicious packages. Like previous attempts, this particular attack starts with copying existing popular libraries and injecting a statement __import__ Malware in an otherwise sane code base.
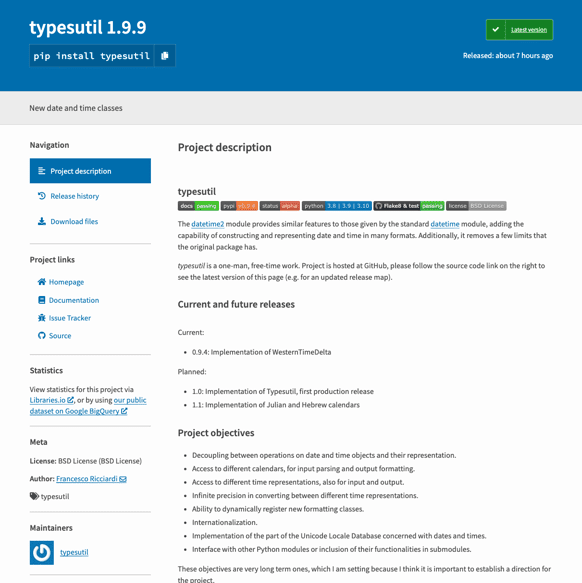
According to the researchers, the advantage of setting up an attack based on copies of an existing legitimate package is that because the package’s home page in the PyPI repository is generated from setup.py And the README.mdIt immediately has a proper homepage with links that work most of the time and everything else. The image above shows the main page of the malicious package’s PyPI Species. You can see that the hacker simply copied the package date and time 2 It made some minor tweaks to make the script consistent with the fake package name it was released with.
“Unless it is closely examined, a quick look at it may lead one to believe that it is a legitimate package as well,” the researchers say. In the report, the researchers detailed the difficulties they encountered while analyzing the obfuscated code of more than 71,000 characters, a “hell of a lot of slime” they had to wade through. In the end, they concluded that the malware distributed by these packages was W4SP Stealer. It is indeed an information theft malware that steals Discord codes, cookies, and saved passwords.

The report notes that in the majority of packages, especially older packages, the malicious import was simply inserted into the file. setup.py where __init__.py. Instead of putting the import somewhere obvious, attackers hide it, making use of the semicolon rarely used in Python to insert malicious code into the same line of legitimate code. In conclusion, here is the exact way this supply chain attack is implemented:
- Dozens of packages are actively launched on PyPI with harmless (some typographical) names that blatantly copy existing legitimate packages and try to sneak a small piece of malicious code into them;
- Malicious code is a statement __import__ cache in files setup.pyAnd the __init__.py or in custom error classes. In either case, it contains the Base64 encoded string being executed. Sometimes, instead of directly importing into these files, it might just be a call os.system() which installs one of its other malicious packages;
- Decoded, this Base64 encoded string contains a Python script written to a temporary file to be executed;
- This temporary file contains code that accesses any number of URLs;
- From each URL it pulls a little obfuscated Python code that implements a compressed byte object;
- If unpacked, this byte object contains the W4SP Stealer malware spread on the system.
According to the researchers, at the time the report was published, the affected packages collectively accounted for more than 5,700 downloads. Note that some of these packages appear to be obvious attempts at typographical attacks like strings And the coloursama (who copies strings And the colorama), which together account for hundreds of millions of downloads per month). In August, Kaspersky Securelist researchers also analyzed PyPI malicious packets that were obfuscated by an open source tool called Hyperion and were detected spreading W4SP malware.
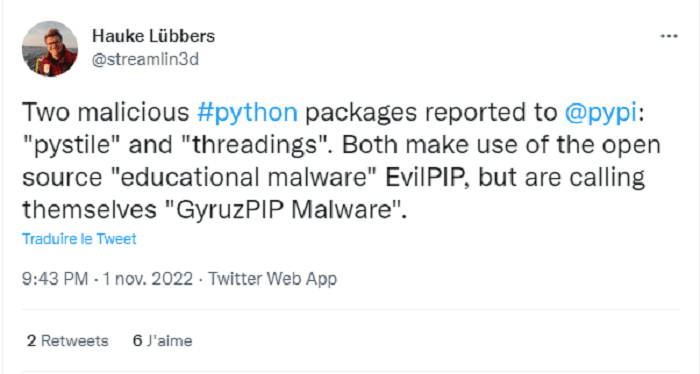
In addition, software developer and researcher Hauke Lbbers has also identified PyPI packages pystile And the strings containing malware that calls itself gyrobeeb. However, the researcher believes that this malware is based on an open source project evil point Published “for educational purposes only”. This week’s development marks another incident in a series of typographical attacks targeting developers while exploiting open source software distribution platforms such as PyPI and npm. Here is a list of packages infected with W4SP that the researchers identified:
- Arithmetic
- coloursama
- coloroen
- Corlaby
- cypress
- duet
- common questions
- Fatnoob
- felpesviadinho
- iao
- incrivelsim
- installpy
- yes
- pydprotect
- Behents
- pyptext
- Bislet
- pystyle
- pystytus
- Berlep
- Requests – httpx
- chasigma
- stringer
- nervous
- sutiltype
- strings
- color type
- printing
- Species
source : Asylum
And you?




See also

“Hardcore beer fanatic. Falls down a lot. Professional coffee fan. Music ninja.”






More Stories
Google has registered a trademark on the name of the AI-generating camera in its next smartphone
Opening concert of the Lanaudiere Festival: Farah Alipay will take us on a journey into space
Hybrid brains were created from rat and mouse cells