Microsoft on Wednesday disclosed details of a now-patched “high-risk vulnerability” in the TikTok app for Android that could allow attackers to take control of accounts when victims click on a malicious link.
“Attacks could exploit the vulnerability to hijack an account without users’ knowledge if the target user simply clicked on a specially crafted link,” said Demetrius Valsamaras of the Microsoft 365 Defender Research Team. He said in writing.
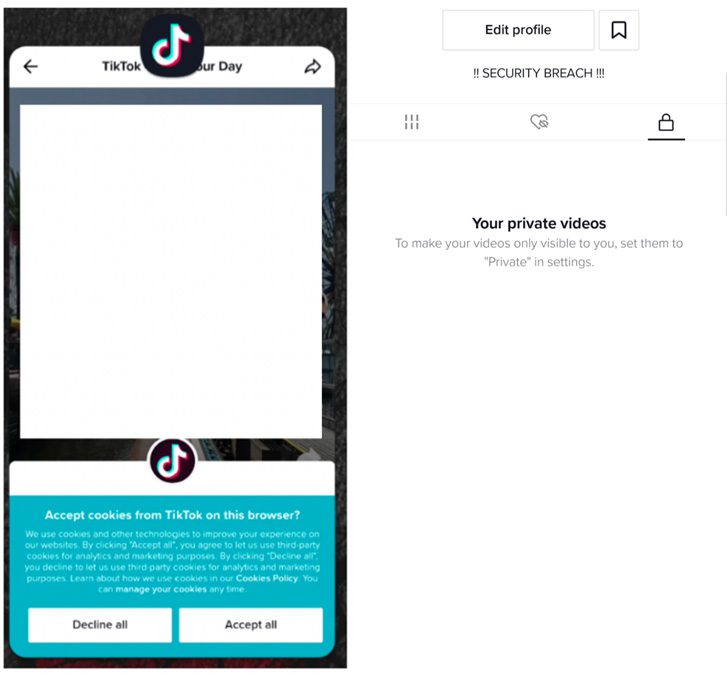
Successful exploitation of the bug could have allowed malicious parties to access and modify TikTok profiles and sensitive user information, leading to unauthorized exposure of private videos. The attackers may also have misused the bug to send messages and upload videos on behalf of users.
– Advertising –
The issue, fixed in version 23.7.3, affects two variants of its Android app com.ss.android.ugc.trill (for East and Southeast Asian users) and com.zhiliaoapp.musically (for users in other countries, except India where prohibited). Combined, the apps have more than 1.5 billion installs between them.
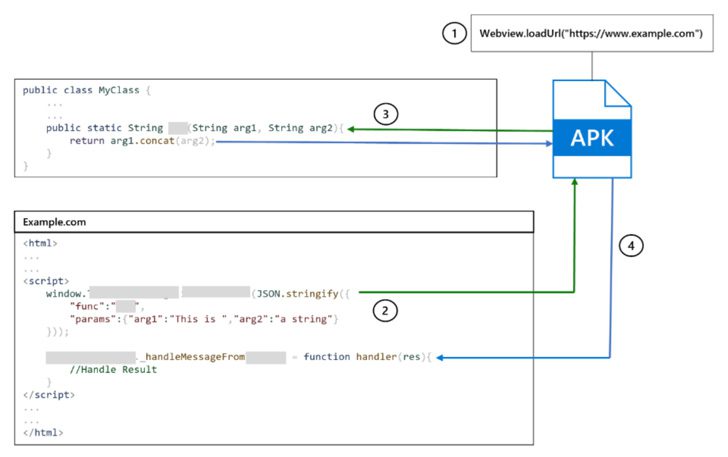
Track K CVE-2022-28799 (CVSS score: 8.8), The vulnerability is related to the application’s handling of a so-called deep link, which is a special hyperlink that allows applications to open a particular resource within another application installed on the device rather than directing users to a website.
“A specially designed URL (unverified deep link) may force WebView com.zhiliaoapp.musically to load a random website,” according to a notice about the flaw. “This could allow an attacker to exploit an attached JavaScript interface for one-click takeover.”
Simply put, the flaw allows bypassing app restrictions to deny untrusted hosts and load any website chosen by the attacker through the Android platform. WebViewA mechanism for displaying web content to other applications.
Valsamaras explained that “filtering is done on the server side and the decision to load or reject a URL is based on the response received from a particular HTTP GET request,” adding that static analysis “indicates that it is possible to bypass server-side validation by adding two additional parameters to the given position link “.
One consequence of this exploit designed to hijack WebView to load rogue websites is that it could allow an adversary to invoke more than 70 exposed TikTok endpoints, harming the integrity of a user’s profile. There is no evidence that the insect was armed in the wild.
Microsoft noted that “from a programming perspective, the use of JavaScript interfaces poses significant risks”. “A compromised JavaScript interface can allow an attacker to execute code using the application’s identifier and its privileges.”

“Hardcore beer fanatic. Falls down a lot. Professional coffee fan. Music ninja.”









More Stories
Why do we feel cramps when we exercise?
We tell you everything!
Yeast can help preserve food